GrapheneOS and forensic extraction of data
GrapheneOS is an Android-based, open source, privacy and security-focused mobile operating system for mobile phones. It is one of the most secure and privacy protecting operating systems (and yes, it does this task comparable and in some scenarios - especially regarding privacy - even better than iOS, but we will come to that later).
However, in the beginning of May, someone started an attack on GrapheneOS across social media platforms. The perpetrators were misrepresenting consent-based data extraction as GrapheneOS being compromised. Which would be funny if it wasn’t so stupid. So let’s see what happened and what actually consent-based data extraction means.
Digital forensics
Digital forensics is the process of uncovering and analysing electronic data in order to gather evidence for legal proceedings. It involves the use of various techniques and tools to examine digital devices such as computers, smartphones, and storage media to identify, preserve, analyse, and present digital evidence.
Digital evidence refers to any data or information that is stored or transmitted in digital form and can be used as evidence in a legal investigation or trial. Digital evidence is often used in criminal investigations to help establish a suspect’s guilt or innocence, and can also be used in civil litigation, regulatory investigations, and other legal proceedings.
Unfortunately, sometimes digital forensics can be abused. It can be used against investigative journalists or political activists, it can be used for privacy violation, to intimidate or harass someone, to tamper with evidence, etc. That is why GrapheneOS developers are working hard to protect mobile phones from tampering and try to make data extraction without user’s consent as hard as possible.
Cellebrite
Cellebrite is a leading Israeli company in the digital intelligence and digital forensics field. Their main digital forensics tool is called Universal Forensic Extraction Device (UFED), and is used to extract and analyze data from mobile devices for investigations.
They are selling their equipment to governments all around the world, and their tools are mostly used for legitimate purposes. Unfortunately they are selling their tools to authoritarian regimes too. Cellebrite’s customer list has included authoritarian regimes in Belarus, Russia, Venezuela, and China, death squads in Bangladesh, military juntas in Myanmar and those seeking to abuse and oppress in Turkey, UAE, and elsewhere.
Data extraction
As mentioned, digital forensics tools first try to extract data from mobile device. This is the initial step in a digital forensics investigation.
The problem for digital forensics is, what if mobile phone is locked? How to extract data from a locked device?
There are several options, but basically three approaches exist.
First option is so called consent-based data extraction. This simply means that user voluntary unlocks their device (or provides PIN code or password), and forensic tool then extracts data from unlocked device.
Why would someone voluntary unlock their device? Well, maybe the owner of the device wants to cooperate with the investigators. Maybe he is a victim of criminal activity and wants to provide evidence against the perpetrators. Maybe he knows that data will prove his innocence. Or something else.
The question is of course, what if user do not want to provide PIN code or password or to unlock their phone?
In that case, there are two general approaches of digital forensic examination. The first option is to try to hack a mobile device so it gets unlocked (and then extract the data). And the other is to try to guess PIN code or password in order to unlock the device and the extract the data.
Companies like Cellebrite are offering various tools, that can try to hack into the locked mobile phone and then extract the data. And their tools also offer a possibility to “guess” PIN code or password, in order to unlock the device.
But first we need to understand that from the digital forensics point of view, mobile phone can basically be in two states.
First is called BFU (Before First Unlock), and it simply means a device that has been turned off or rebooted and never subsequently unlocked by entering the correct PIN or passcode. The second is called AFU (After First Unlock), and it means that device has been unlocked after reboot (meaning that encryption keys are stored in internal memory of the device).
Technically, there is important difference between the two. BFU devices (that hasn’t been unlocked with a PIN or passcode) mostly contains encrypted data. Since the first unlock of the device also decrypts the device (technically: unlocks the decryption key, so device can access the data stored in internal storage), most data on the device in that case is inaccessible for forensic analysis. Technically that means that data are encrypted at rest.
AFU devices (that has been unlocked with the correct passcode after powering on, or restarting) contains decryption key in it’s internal memory, and that key is used to decrypt files in internal storage. In that case most data on the device becomes accessible for forensic analysis, because data in that state are decrypted for normal use. However, in that case screen lock could still been activated, meaning, that forensic investigator needs to unlock the screen first, and then can extract the data.
From the user’s point of view this simply means that a locked device in BFU state presents significant challenges for data extraction, while an unlocked device (in AFU state) offers greater access to extract the data.
Data extraction approaches
As already mentioned, AFU devices are easily approached for extraction. General approach here is to hack into the locked mobile phone (by exploiting some software vulnerability) in order to disable or bypass a screen lock, and then extract the data.
In case of BFU devices, where data in internal storage are still encrypted, the forensic examinator needs to “guess” PIN code or password, in order to unlock the device. Usually this is done by so called brute forcing. This simply means that a forensic tool tries to guess the correct PIN or password by going through all possible combination, until the correct one is found.
Cellebrite’s capabilities
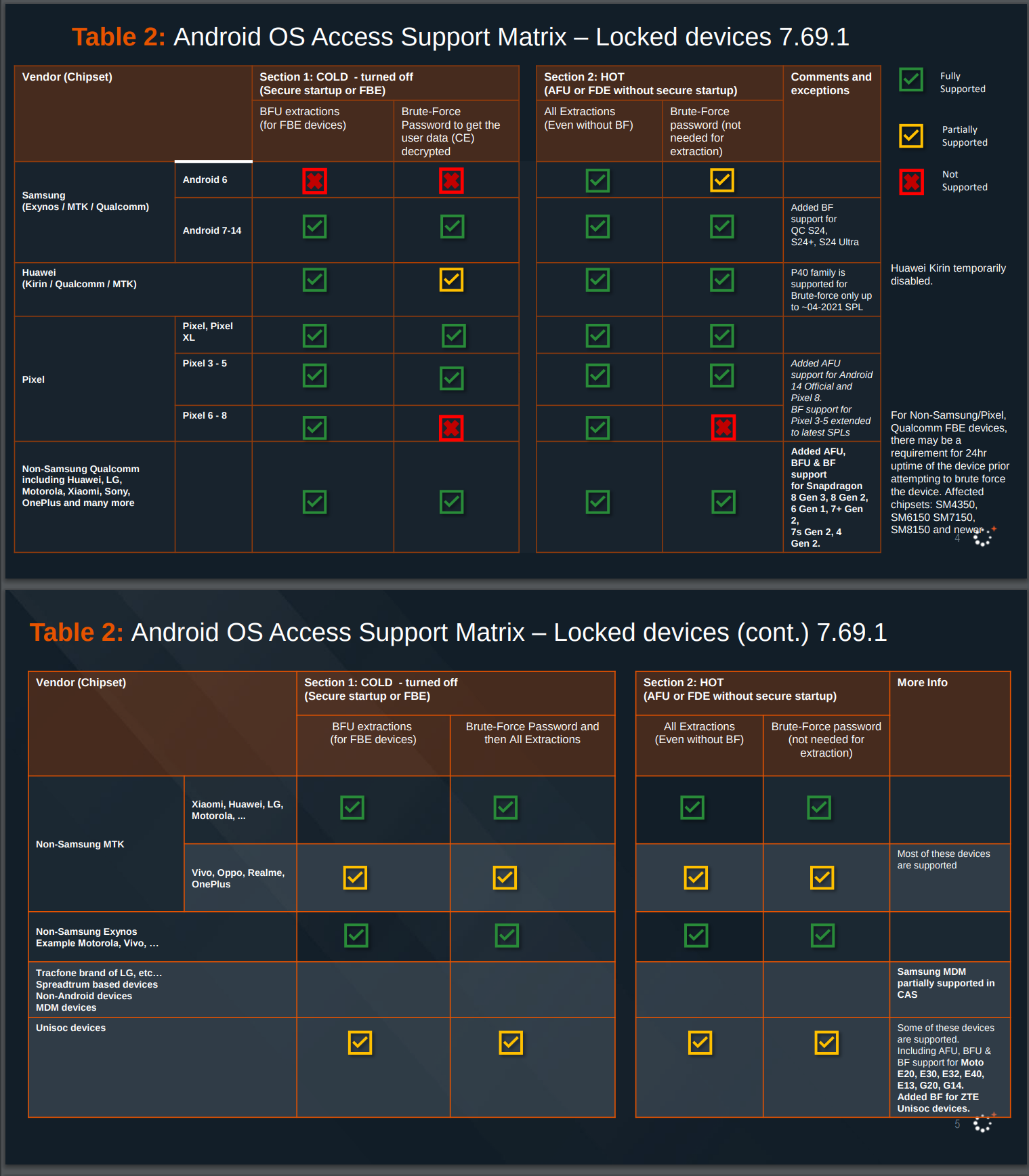
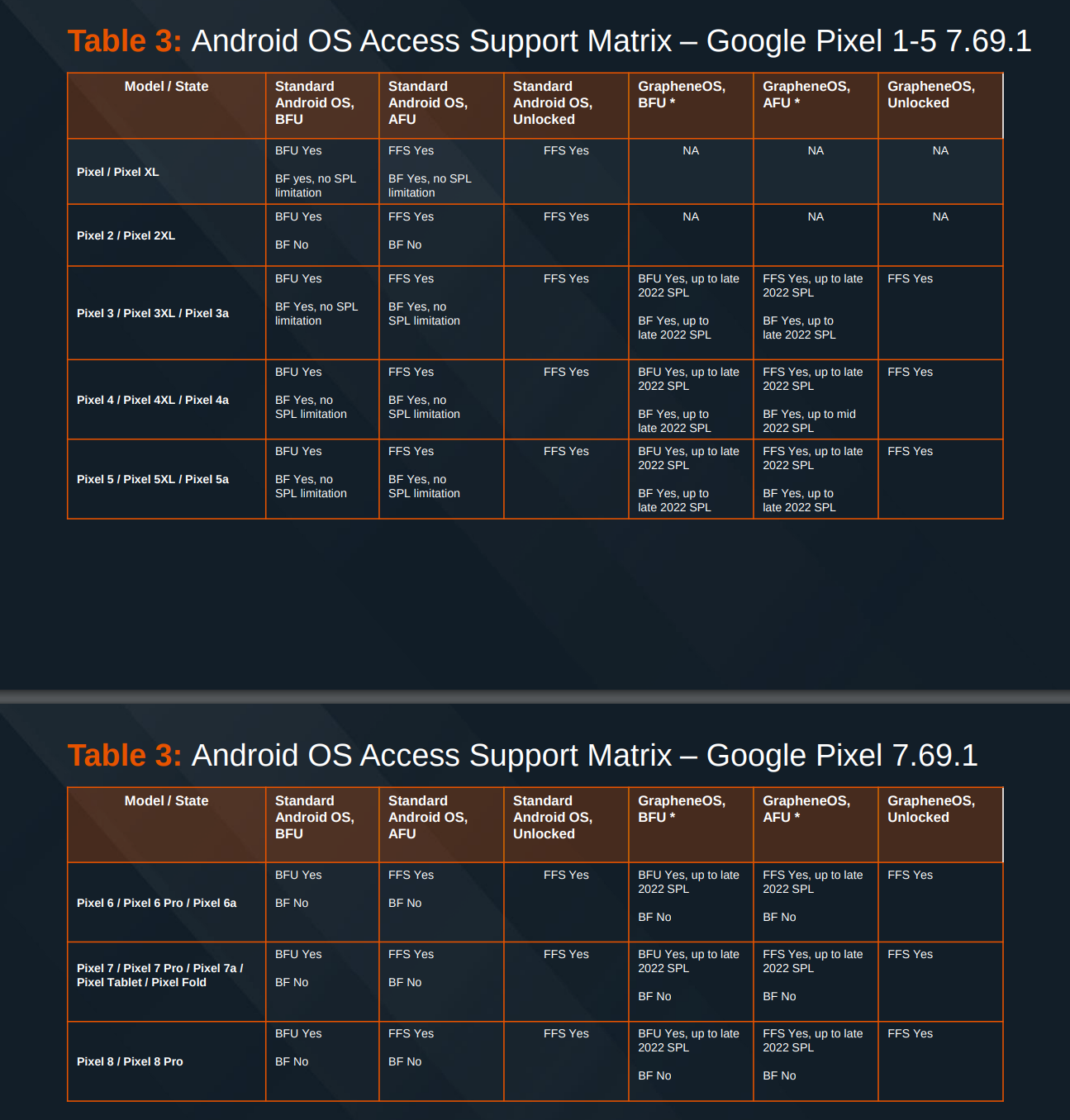
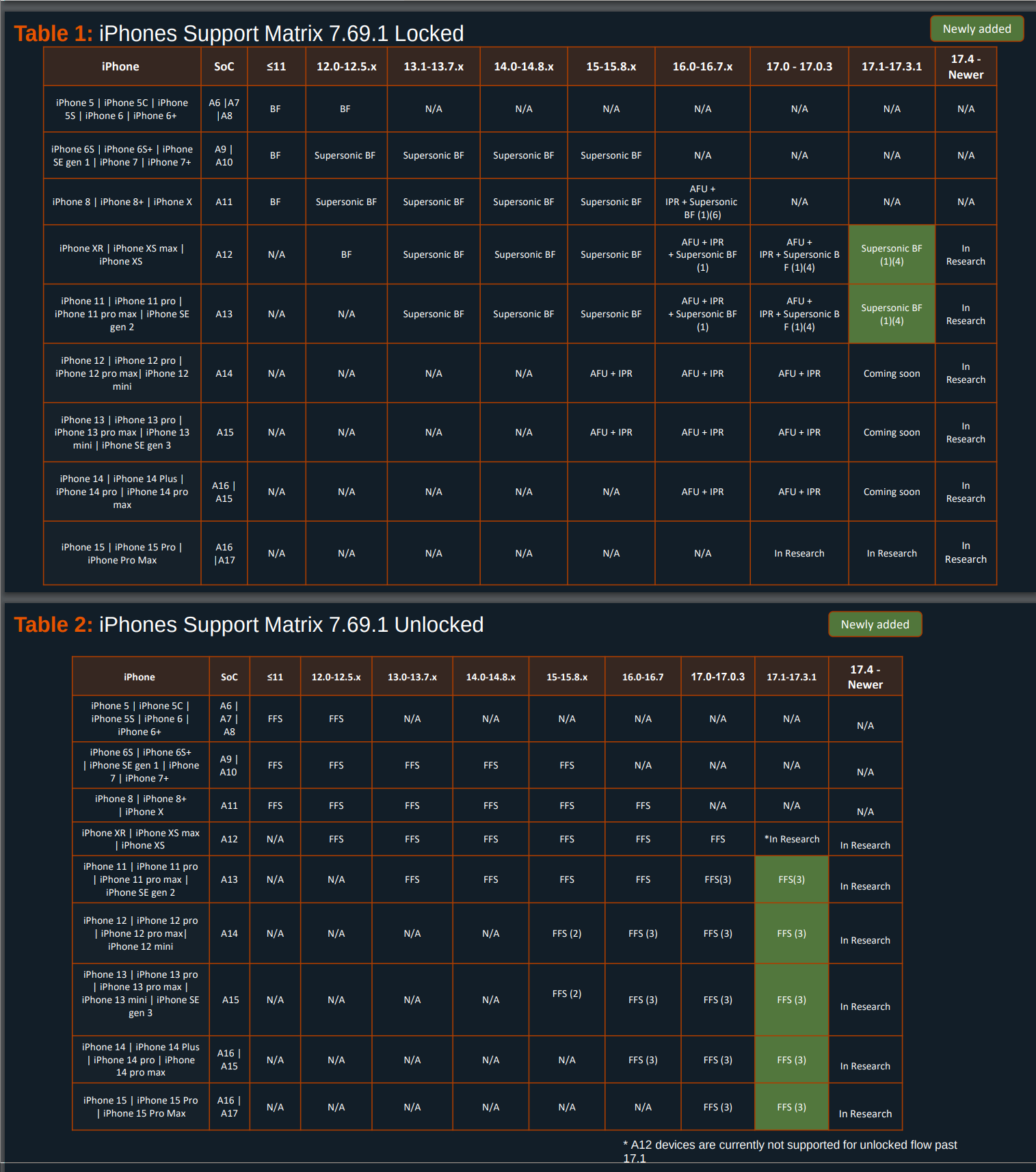
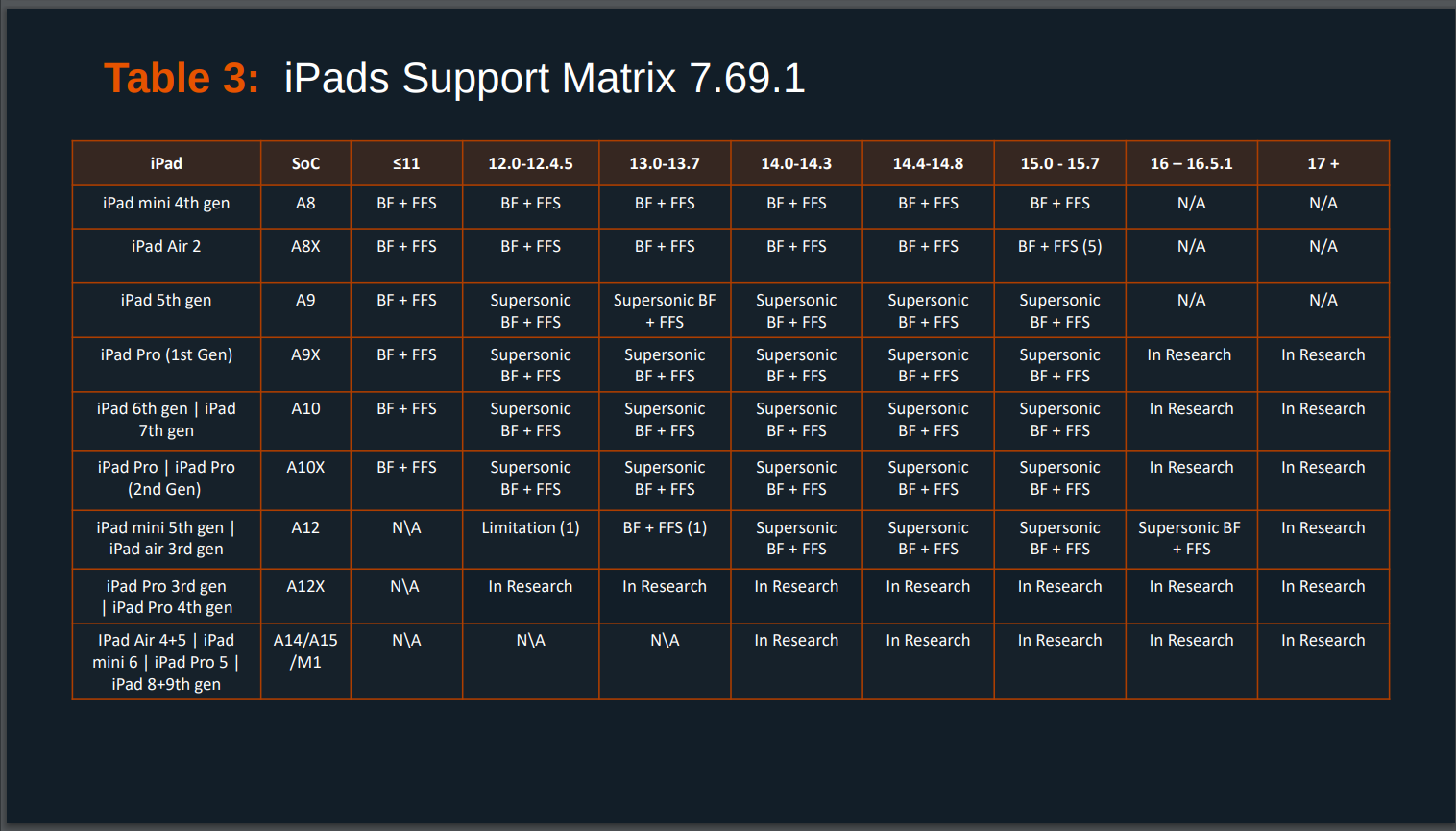
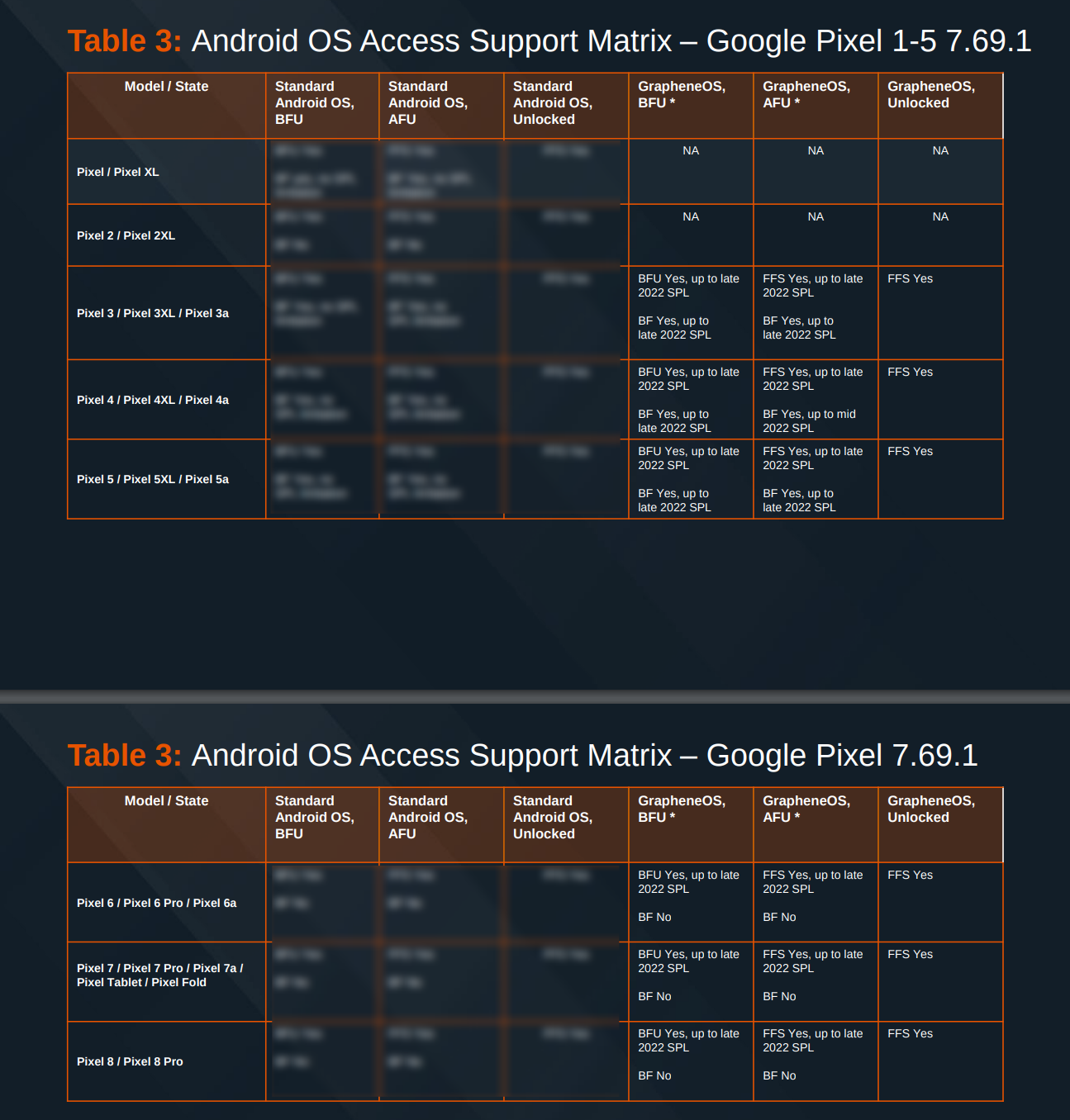
In April 2024 Cellebrite published a list of their capabilities provided to customers. The list shows that they can successfully exploit every non-GrapheneOS Android device brand. They can do this for devices in AFU and BFU states. This means, that Cellebrite’s tools can unlock (and then extract data) every Android device on the market.
According to Cellebrite’s documents, they have similar capabilities for iOS devices too. Not all, but for many of them. In fact, it is only the latest device generation and OS versions which are not fully supported yet (however, it is fair to mention, that most iPhone users are getting iOS updates automatically). Will they be able to develop exploits for the later iOS devices too? We do not know that, but we know, that NSO (an Israeli company developing Pegasus spyware) already did that, right after iOS 17 has been released in September 2023.
Which is interesting, because Apple is advertising iOS as “the world’s most personal and secure mobile operating system”.
What about GrapheneOS? According to the documents, Cellebrite admits they can not hack GrapheneOS if users had installed updates since late 2022. This is important, because GrapheneOS is releasing security updates and improvements quite frequently - sometimes even several times a month. And GrapheneOS is designed in such a way, that updates are automatically enabled, and if users want to disable them, they need to do that manually. This means that very likely vast majority of users have GrapheneOS updated to the last version automatically and their phones can not be hacked by Cellebrite’s tools.
On the other side, Cellebrite claims that they can do so called consent-based full filesystem extraction with iOS, Android and GrapheneOS. As already mentioned, this simply means they can extract data from the device once the user voluntary unlocks their device. For GrapheneOS that means, that when they get unlocked phone, they just enable developer options and use standard ADB tool (ADB lets you communicate with Android devices through a computer) to extract the data.
So, according to Cellebrite documents, they can not unlock fully patched GrapheneOS phone, unless user voluntary unlocks the phone. In fact, analysis of Cellebrite’s documents shows, that they even can not brute force a random 6-digit PIN on Pixel 6 and later phones (which are the phones supported by GrapheneOS). Cellebrite’s documents reveal, that Pixel 6 phones and later with GrapheneOS (and the latest iPhones also), are the only devices where a random 6 digit PIN can not be brute forced.
The attack on GrapheneOS on social media?
As we mentioned at the beginning, in the beginning of May, someone started an attack on GrapheneOS across social media platforms. The perpetrators claimed that GrapheneOS has been compromised, and the “proof” has been, that data extraction from GrapheneOS is successful when it is consent-based.
It is unclear who has been behind this social media attack, but in December 2020 something similar happened. At that time, various media (including BBC) reported, that Cellebrite claimed to have cracked Signal’s encryption. Signal is a free, encrypted messaging application, which is widely considered one of the most secure messaging apps due to its strong encryption and focus on privacy.
However, at that time it turned out, that the claims were completely false - Cellebrite has been able to extract Signal messages only if user unlocked the phone and Signal app and hand it to the forensic examinator. Which is by definition consent-based extraction and does not really require some specific technical excellence from the forensic acquisition tool.
Short notice: Signal’s local database on a phone is encrypted. So you need to need to extract the Signal database from the filesystem first, and then to you need to obtain three values to decrypt the database. The first is stored in so called Keystore system, and the other two values are stored in the XML file on the phone’s file system. It is important to know that cryptographic keys stored in a Keystore system are more difficult to extract from the device, because once keys are in the Keystore, you can use them for cryptographic operations, with the key material remaining non-exportable.
Defense against forensic hacking tools in GrapheneOS
Now let’s dive into GrapheneOS security countermeasures against described attacks.
Protection against hacking into the phone
GrapheneOS has implemented many security features. You can get a glimpse of them from my presentation on GrapheneOS security.
However, regarding various forensic tools, it is important to mention, that GrapheneOS has a special feature that disallows new USB connections in AFU mode (After First Unlock) after the device is locked, and fully disables USB data at a hardware level once there aren’t active USB connections. This means that if an attacker would connect GrapheneOS device to the computer through USB, GrapheneOS device will not allow any connection at all.
Users can set it to do this in BFU (Before First Unlock) mode or even when the phone is fully unlocked. And users with a high threat model can even fully disable USB, including USB-PD/charging, while the OS is booted. So they can decide to only allow charging while powered off or booted into the fastboot/fastbootd/recovery/charging modes. This is the feature no other phone has, and can be completely customized by the user.
GrapheneOS is constantly improving security, and since beginning of 2024 they massively improved security against various possible exploits. In April 2024 they also helped to implement several firmware improvements for Pixel phones.
Protection against brute force attacks
As we mentioned, in case of BFU devices, where data in internal storage are still encrypted, the forensic examinator needs to “guess” PIN code or password, in order to unlock the device. This is done by so called brute force attack (guessing every possible combination of PIN code or password).
However, Pixel 6 and later phones contain a dedicated security chip Titan M2, also called hardware security module, which is storing the decryption keys. This chip will unlock the internal phone storage only if user will enter the correct PIN or password.
But here is the catch. If an attacker try to perform brute force attack (i. e. try to go through all possible PIN/password combinations), the chip will limit the number of attempts. After 5 failed attempts, chip will add 30 second delay before next guessing attempt is allowed. Then delay gets increased (after 30 failed attempts the delay doubles after every 10 attempts), and after 140 failed attempts, GrapheneOS and its secure element will limit brute force to 1 attempt per day. This is called secure element throttling.
So if an attacker would like to test all different combinations to guess a 6-digit PIN, there are one million possible combinations, so brute forcing would take a long, long time. Unless, the attacker is extremely lucky and guesses the correct PIN at the few first attempts.
Of course, the question is, is it possible to somehow hack this secure element or unlock the limited number of attempts? The answer is - very unlikely. Why? Because this secure element has been developed specifically to protect against those types of attacks. And it has passed the highest hardware vulnerability assessment (AVA_VAN.5) by an independent and accredited evaluation lab.
In fact, GrapheneOS is so successful in this area, because it is doing far more hardening than iOS against these attacks. iPhones also have security element, but the companies developing attacks, had successfully bypassed secure element throttling from Apple for years (and are doing the same with Samsung and Qualcomm implementation of secure element). These companies were successfully bypassing the secure element throttling on 2nd through 5th generation Pixels. Pixel 2 used NXP secure element and Pixel 3 moved to a custom ARM secure element. But Pixel 6 and later phones are using a custom RISC-V secure element. It seems that moving away from the standard ARM Cortex secure element cores was the correct decision, because it blocked these companies from successfully exploiting the secure element for several years.
Auto reboot feature
GrapheneOS also has an auto-reboot feature, meaning that after some time, phone gets automatically rebooted. Default auto reboot time is 18 hours (if phone is not unlocked in that time, it will reboot), but user can set it to a different interval, even as low as 10 minutes.
This technically means that the data after this period are put back to rest, or, to put it differently, phone gets from AFU to BFU state. And as we already explained, a locked device in BFU state presents significant challenges for data extraction, much more than unlocked device in AFU state.
After reboot, it is almost impossible to extract decrypted data from the phone. So the focus of GrapheneOS’s team is defending against exploitation long enough for auto-reboot to work, and after that your data are even safer than before. That means that if an attacker develops a successful exploit, their window of opportunity to use it to get data from user profiles is until next reboot from when the phone was locked.
Conclusion
In the last year, GrapheneOS started to put much more effort into defending your phone against these attacks. Users who need their data secure, should definitely use a strong passphrase. To make that more convenient, GrapheneOS is developing 2-factor fingerprint unlock feature, which will allow people to combine a strong passphrase with convenient fingerprint and PIN unlock. They are also planning to offer an UI for generating random passphrases automatically. This will vastly improve security and make access to the user’s data on a phone much more difficult.
The actors that want to hack into GrapheneOS are rightfully desperate. So it is no surprise, that they try to play dirty, by spreading misinformation. But knowledge is power and misinformation could be successfully fought with facts.
Ključne besede: kriptografija, mobilna telefonija, GrapheneOS